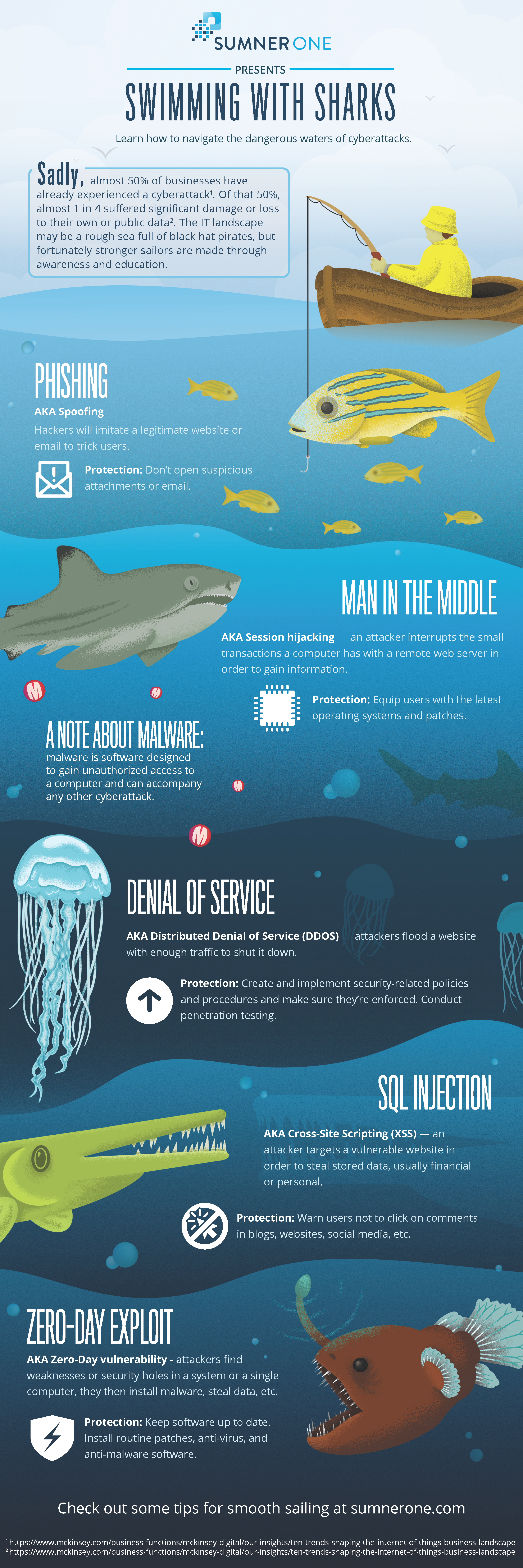
Cybersecurity is the practice of protecting electronic data and systems from a cyberattack. Having a robust cybersecurity framework is vital to protect sensitive information. Sadly, almost 50% of businesses have already experienced a cyberattack. Of that 50%, nearly 1 in 4 suffered significant damage or loss to their own or public data. The IT landscape may be a rough sea full of black hat pirates, but fortunately, stronger sailors are made through awareness and education.
Understanding the types of cyberattacks that exist is the first step to being a smart end user. End users are the first line of defense in any cybersecurity plan. Knowing what you’re looking for, what types of files to report to IT staff before those files gain unauthorized access to your system, and how to provide the minimum levels of protection can be the difference between keeping sensitive data secure and a possible breach.
Types of Cyberattacks
There are many types of cyberattacks—this list below is by no means exhaustive. These attacks can be used in combination with each other, too. For example, a bad actor (AKA cybercriminal) may send emails that have been spoofed in a phishing attack to deploy malware throughout an organization’s network. How would you defend against an attack like this? Don’t open any attachments that look suspicious. Don’t open an email from an address you don’t recognize. When in doubt, report anything to your IT staff.
Malware
- Malware: software designed to gain unauthorized access to a computer
- Malware can accompany any other cyberattack.
- AKA ransomware—bad actors hijack systems for a payout
- Protection: Don’t click on suspicious files or open downloads to avoid malware.
Phishing
- AKA Spoofing—hackers will imitate a legitimate website or email to trick users
- Protection: Don’t open suspicious attachments or email.
Man in the Middle
- AKA Session hijacking—an attacker interrupts the small transactions a computer has with a remote webserver to gain information
- Protection: Equip users with the latest operating systems and patches. Make sure your computer is up to date by checking with your IT department.
Denial of Service
- AKA Distributed Denial of Service (DDOS)—attackers flood a website with enough traffic to shut it down
- Protection: Create and implement security-related policies and procedures and make sure they’re enforced. Conduct penetration testing.
SQL Injection
- AKA Cross-Site Scripting (XSS)—when an attacker targets a vulnerable website to steal stored data, usually financial or personal
- Protection: Warn users not to click on comments in blogs, websites, social media, and other online platforms.
Zero-Day Exploit
- AKA Zero-Day vulnerability—attackers find weaknesses or security holes in a system or a single computer, they then install malware and steal data.
- Protection: Keep software up to date. Install routine patches, anti-virus, and anti-malware software.
When you don’t have the knowledge and understanding, the world of cybersecurity can be scary. The best protection is awareness and education. Training users, providing them with tools, and updating old systems are great ways to get started keeping your business’ data safe.
Using a visual reference can be helpful, and SumnerOne has created an infographic to drive this information home. Swimming with Sharks is a visual representation of the types of cyberattacks within the dangerous waters of the cybersecurity landscape. There can be bad actors lurking anywhere, from the surface to the deep waters of the dark web. Click the image to download your copy. Print them for your end-users, so they never forget that they are the first line of defense in a successful cybersecurity plan of attack.
SumnerOne is your partner for cyberattack awareness and prevention. Check out some tips for security education and cyber defense here.
If you’d like help with cybersecurity education, let SumnerOne be your compass. Contact us today.
 FREE EBOOK DOWNLOAD
FREE EBOOK DOWNLOAD